Introduction
Web Application Firewalls (WAFs) protect websites and APIs from malicious attacks, but understanding their alerts and logs often requires familiarity with specific security terms. Two of the most common terms you’ll encounter are “False Positive” and “Threat Score.” Knowing what these terms mean—and how to interpret them—can help you fine-tune your WAF settings and strengthen your web security strategy.
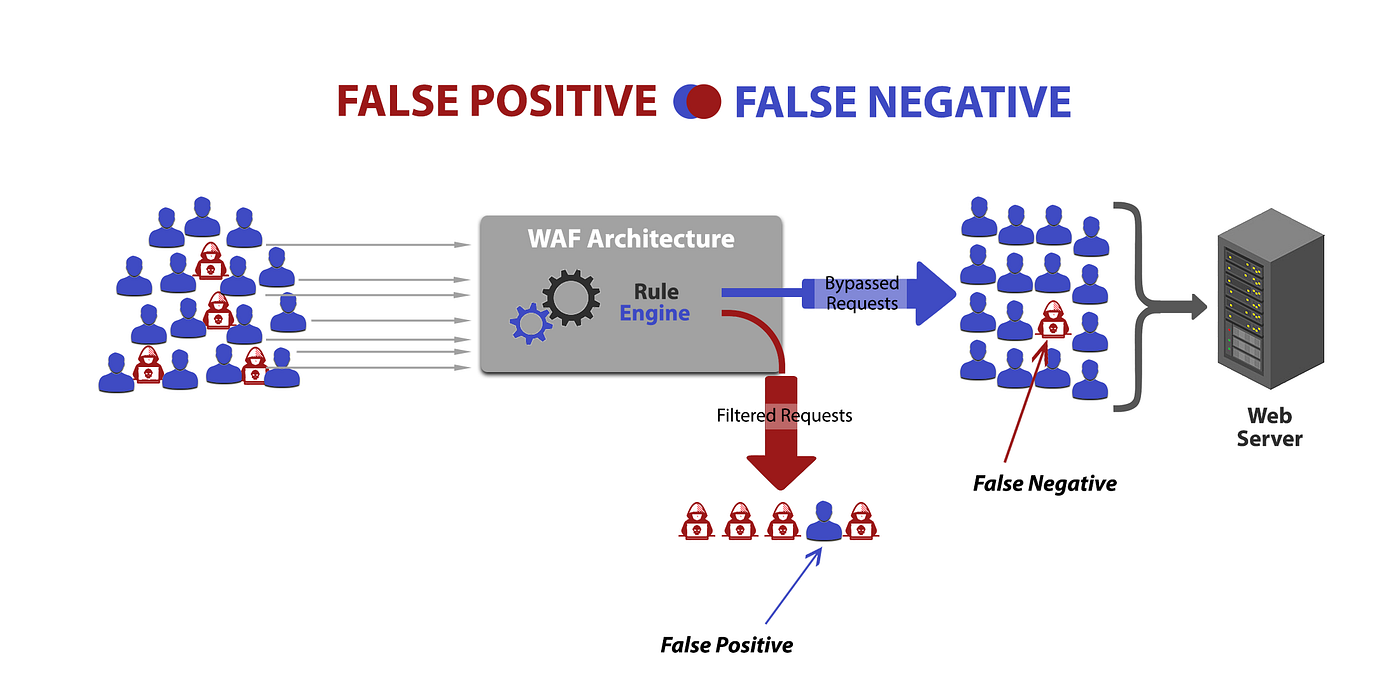
What Is a False Positive?
A false positive occurs when the WAF mistakenly blocks or flags a legitimate request as malicious. This can happen when security rules are too strict or if normal user behavior appears suspicious to the WAF.
Common Causes of False Positives
- Custom User Inputs: Forms or URLs containing characters like
<script>or SQL keywords may trigger WAF filters. - APIs and JSON Payloads: Complex data structures can resemble attack patterns.
- Misconfigured Rules: Default WAF rules may not suit every web application’s unique behavior.
Why False Positives Matter
False positives can:
- Block real users or business-critical traffic
- Cause frustration and lost conversions
- Waste time on unnecessary investigations
To manage false positives, WAF administrators often adjust rule sensitivity, whitelist trusted patterns, or implement positive security models.
What Is a Threat Score?
A threat score is a numeric value assigned by the WAF to a request based on its potential maliciousness. The higher the score, the more likely the request is considered dangerous.
How Threat Scores Work
Each incoming request is analyzed for suspicious patterns, such as:
- SQL or XSS injection signatures
- Known bad IP addresses or geolocations
- Unusual request rates or headers
Based on these signals, the WAF assigns a score—often on a scale from 0 to 100.
Using Threat Scores Effectively
- Set Thresholds: Block requests only above a certain score (e.g., ≥70).
- Monitor Behavior: Investigate medium-score events instead of immediately blocking.
- Automate Responses: Apply rate limits, challenges (e.g., CAPTCHA), or flagging based on score ranges.
False Positives vs. Threat Scores
While false positives represent mistakes by the WAF, threat scores are part of a predictive model. One aims to reduce errors, the other helps gauge risk. Together, they provide a balance between protection and usability.
Conclusion
Understanding what “false positive” and “threat score” mean in your WAF environment is crucial for effective web security. By minimizing false positives and properly interpreting threat scores, you can fine-tune your protection to keep threats out—without locking out your users.