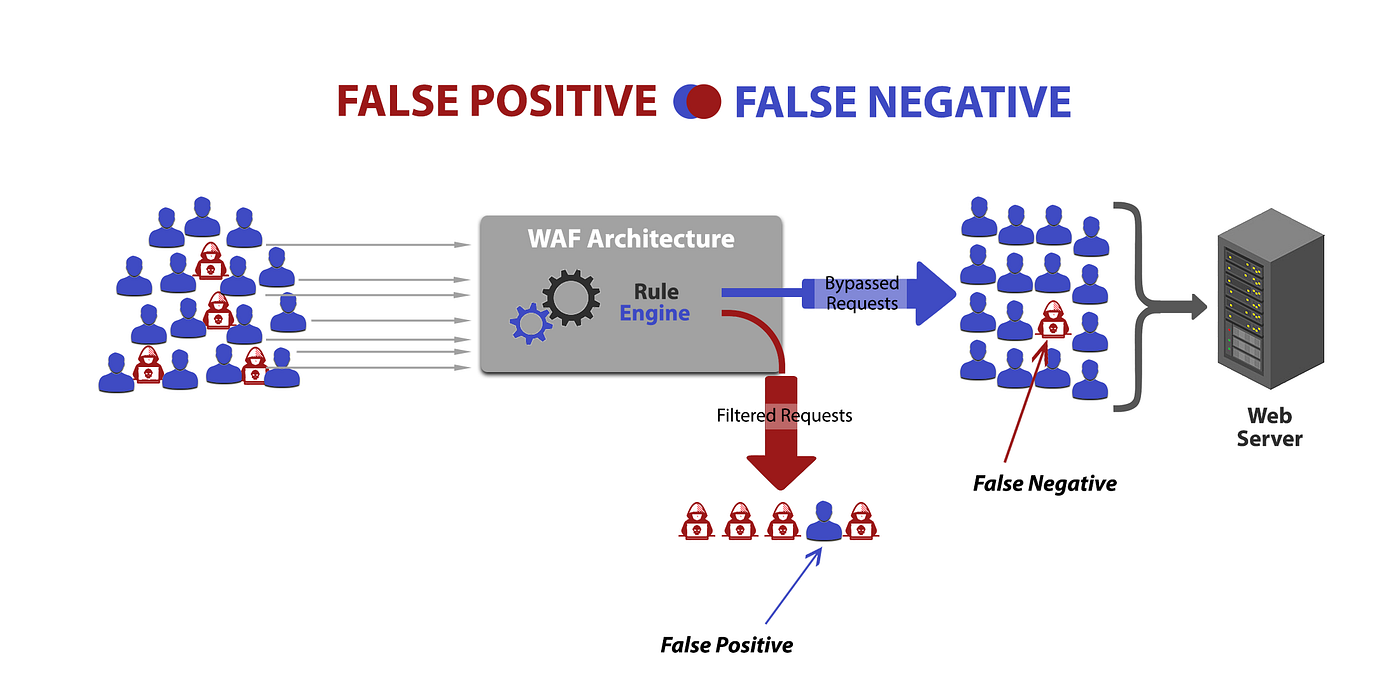
Introduction
As modern applications rely more heavily on APIs—especially REST and GraphQL—they’ve become prime targets for cyberattacks. Web Application Firewalls (WAFs) have evolved to address these threats by inspecting API traffic and enforcing security rules. However, protecting APIs requires understanding their unique risks and how WAFs can be tuned accordingly.
Why APIs Need WAF Protection
Unlike traditional web pages, APIs expose structured data and often bypass conventional user interfaces. This makes them vulnerable to:
- Injection attacks (SQL, NoSQL, command injection)
- Excessive data exposure
- Broken authentication or authorization
- Rate abuse and denial-of-service (DoS)
A WAF provides an application-layer defense that filters malicious requests, enforces authentication policies, and logs suspicious behavior in real time.
REST API Threats and WAF Mitigation
REST APIs use predictable HTTP methods (GET, POST, PUT, DELETE) and URL structures. Common threats include:
1. Parameter Tampering
Attackers manipulate query or path parameters to alter server behavior. A WAF can validate expected parameter formats and block anomalies.
2. Injection Attacks
Unvalidated inputs can lead to SQL or NoSQL injection. WAFs detect payload patterns and block malicious syntax before it hits the backend.
3. Lack of Rate Limiting
Without controls, APIs can be spammed with thousands of requests. A WAF can enforce rate limits, throttling, or CAPTCHA challenges to stop abuse.
GraphQL API Threats and WAF Challenges
GraphQL APIs offer flexible querying power—but this flexibility can introduce complex attack vectors. Threats include:
1. Query Depth Attacks
GraphQL queries can nest recursively, potentially overwhelming servers. WAFs with schema awareness can block overly deep or complex queries.
2. Introspection Misuse
GraphQL introspection reveals schema details, which attackers can use to map endpoints. WAFs can disable introspection in production or alert when it’s accessed.
3. Mass Data Exposure
GraphQL allows clients to fetch large amounts of data with one query. A WAF can set object limits, query size caps, and enforce field-level permissions.
Best Practices for Securing APIs with WAF
- Enable API-specific rulesets: Use your WAF’s REST or GraphQL protection modules if available.
- Whitelisting and schema validation: Only allow known, expected input structures.
- Rate limiting and behavioral analysis: Throttle traffic and detect abnormal access patterns.
- Log and monitor requests: Use WAF analytics to investigate anomalies and attacks in real time.
- Integrate with API gateways: Enhance security by pairing WAFs with API gateways for deeper inspection and identity management.
Conclusion
REST and GraphQL APIs are essential to today’s applications—but they come with unique security challenges. A properly configured WAF can mitigate many of these risks by enforcing strict rules, validating requests, and blocking malicious behavior. As API adoption grows, integrating WAF into your API security strategy is no longer optional—it’s essential.